The electronic signature in Sloneek complies with the EU eIDAS standard. In the application it is possible to electronically sign Contracts, confirmation of reading / acceptance of a document or handover protocol of work tools.
The legal opinion of the renowned AK Bříza & Trubač on the validity of electronic signatures by users of Sloneek can be viewed HERE. More legal comments can be seen and translated HERE.
Document signature security in Sloneek
Sloneek Europe s.r.o., the company operating the application (hereinafter Sloneek), acts as a processor of personal data. The company that enters its employees and collaborators into the application then acts as a controller.
Users of the application are therefore set up by an authorised person on the customer (company) side, who, when setting up a company account, agrees to the general terms and conditions, which also include the treatment of data protection.
 Creating a user
Creating a user
The fact that the user is created by the company is the first step in the verification of the user's identity, since it can be assumed that the company will only create the user and pay the monthly license for the user based on some relationship between the company and the user.
The fact of the user's creation, including the exact wording of the user's email address, first and last name, is recorded in the application's audit log. The audit log is user immutable, i.e. the company and its users cannot do anything with it except read it.
The user is invited into the application after it is created via an automatic email notification that contains a unique token for the user's first password setting. The password must meet the parameters for sufficient length.
An audit trail, is usually an automatically and chronologically recorded set of records about the activities, actions of someone or something. An audit trail serves as evidence that something happened or someone did something.
 User password setting and login
User password setting and login
The user receives a notification prompting them to set a password and log in for the first time. Both of these are recorded in the audit log with an appropriate timestamp.
Logging into the application is only possible using a valid username (which consists of the user's email) and password. A user who has entered the application in this way is therefore fully authenticated (verified).
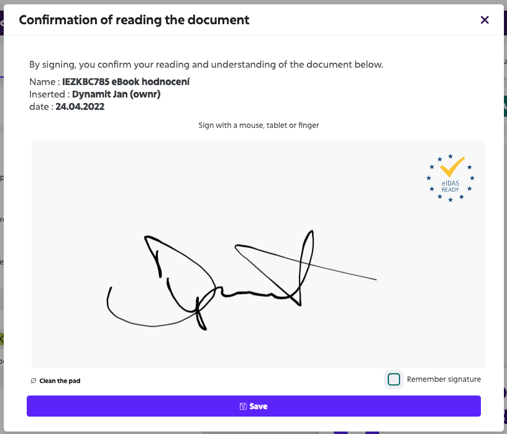
 Signing the document
Signing the document
The user receives an email notification which, after logging in, takes him to a section where he can read the document waiting for his signature.
After reading, he clicks on the Sign button. Depending on the setup of the particular document or Signature Workflow that requires the user's signature, he is either prompted to type his signature (with a computer mouse, stylus, or finger) on the screen, or is simply prompted to confirm the action by selecting the confirmation button.
At that point, a single page with the user's signature is added to the document, which must always be an open PDF (no edit lock, no pages deleted after the PDF is generated).
This page contains a time stamp, and if the user has signed with a handwritten signature, this signature, as well as identifying information about the document and the user, and the cryptographic hash of their signature.
The fact that:
- the user has logged into the application,
- the user has viewed the document ❇️
- the user has signed with a typed signature or confirmed with the button ❇️
is kept in the audit log. Points marked with an asterisk ❇️ are accessible within the audit log to all users who have access to the signed document.
 Signing by other users
Signing by other users
Within the signature workflow, the user does not have to sign alone, but other users within the same corporate account can be selected by the document creator for signing. Each additional signed user will then automatically attach their signature page as described in section 3.
In the case of a signature request by an external user who is not established in Sloneek, the founder of the signature workflow adds such a user using only first name, last name, phone number and email. A notification message will be sent to that user with a link to sign the document. Once clicked, he fills in the first name, last name and phone number. The last step of authentication is to enter the SMS code sent. He can then sign the document.
 Generation of the final document
Generation of the final document
Contracts
Once the contract signature workflow is complete (at the time of the last signer's signature), the final document is generated, which contains all pages of the original document and one page with the signature and identification information for each signer.
The signed document is inserted into the document library of each signatory. For signers who do not have an account in the application, the signed document arrives in the email embedded in the pre-signature verification.
Other documents and handover logs
After confirming the reading of a document or receipt of an asset, a signing log is saved for each document or asset.